Chef InSpec is an open-source testing framework for infrastructure with human as well as machine-readable language for specifying compliance and security policy requirements. Chef InSpec works by comparing the actual state of your system with the desired state which is expressed as easy-to-read and easy-to-write code. It detects violations and displays findings in the form of a report that offers insights for remediation.
Chef InSpec has over 500 ready-to-use resources, that include AWS, Azure, and GCP (Google Cloud Platform) cloud resources.
Setting up the Environment
Install Chef Workstation - It is a collection of developer tools that enable devices in your fleet to interact securely with your Chef Server. It includes Chef Knife, Chef InSpec, Cookstyle, Chef Habitat, and Test Kitchen. It also includes Ruby and other dependencies, so you don’t have to install anything else to get started with all the Chef tools.
InSpec resource pack uses the AWS Ruby SDK (Software Development Kits) which makes it easy to write tests for resources in AWS.
AWS Credentials
Valid AWS credentials are required, see AWS Documentation
Configure your AWS credentials in ~/.aws/config and ~/.aws/credentials file
~/.aws/config
[default]
region = us-east-1
~/.aws/credentials
[default]
aws_access_key_id = AKIAXHDZZ2KLTYNX7IKVF
aws_secret_access_key =
5HiEwCYKEGchdwFDaFYgjuo6UZs05vnyGIEKZ5zY
Each resource requires specific permissions to perform necessary testing operations. For example, to test an AWS EC2 instance, your service principal requires the ec2: DescribeInstances and iam:GetInstanceProfile permissions.
To use AWS resources in your test, first generate an inspec.yml file using
$ inspec init profile --platform aws my-cloud
Edit the inspec.yml file to include the following:
name: my-cloud
title: Cloud test
maintainer: Akshay
copyright: Akshay
Copyright_email: akshay@chef.com
license: Apache-2.0
summary: An InSpec Compliance Profile For AWS
version: 0.1.0
inspec_version: '~> 4'
depends:
- name: inspec-aws
url: https://github.com/inspec/inspec-
aws/archive/main.tar.gz
supports:
-platform: aws
URL - https://github.com/inspec/inspec-aws/archive/main.tar.gz will contain all the necessary libraries, Gem files and master inspec.yml file to execute a cloud control file.
If a resource is local, change the URL to path to:
name: my-cloud
title: Cloud test
maintainer: Akshay
copyright: Akshay
copyright_email: akshay@chef.com
license: Apache-2.0
summary: An InSpec Compliance Profile For AWS
version: 0.1.0 inspec_version: '~> 4'
depends:
- name: inspec-aws
Path: ../my-cloud
supports:
- platform: aws
Edit the control file to include your test cases.
Example:
title ‘Cloud test’
describe aws_ec2_host(host_id: 'i-00cf29b8e2cc633e7') do
it { should_not exist }
end
Check the syntax of your files using cookstyle -a command
Execute the profile using the command inspec exec my-profile -t aws://
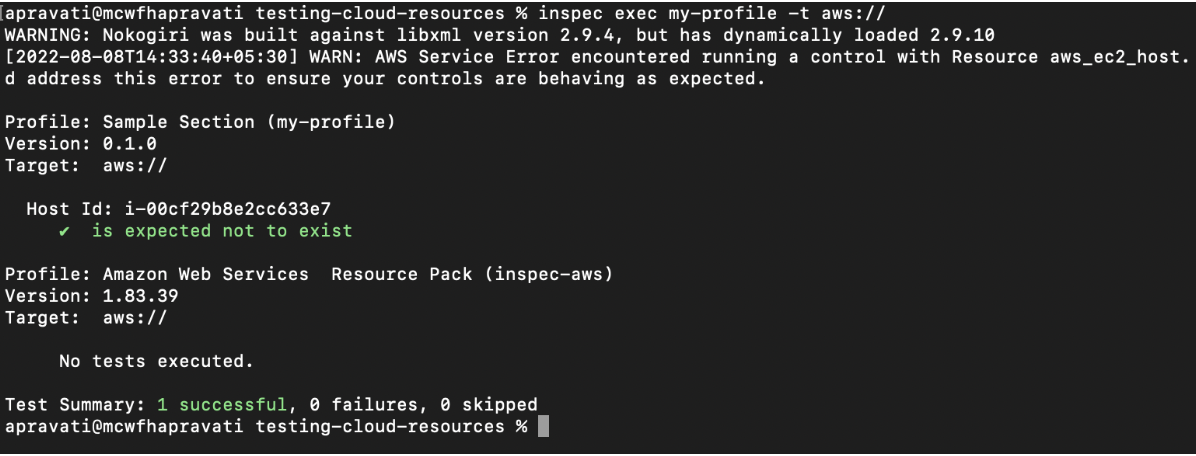
You can also add attributes to your inspec.yml file which would make the command more robust while accepting inputs from the users.
name: my-cloud
title: Cloud test
maintainer: Akshay
copyright: Akshay
copyright_email: akshay@chef.com
license: Apache-2.0
summary: An InSpec Compliance Profile For AWS
version: 0.1.0
inspec_version: '~>
4'
depends:
- name: inspec-aws
url: https://github.com/inspec/inspec-
aws/archive/main.tar.gz
supports:
- platform: aws
attributes:
-name: bucketname
description:
“S3 bucket name”
required: true
value: $DEV_BUCKET
type: string
Edit the control file to check for the bucket name and its existence.
bucketname = attributes(‘bucketname’)
control “AWS S3” do
impact 1.0
title “Cloud test”
describe aws_s3_bucket(bucket_name: bucketname) do
it
{ should exist }
it { should_not be_public }
end
end
To execute and run Inspec test, use the command:
inspec exec aws-resources -t aws:// --input
bucketname="s3_bucket_name"
If you created a GitHub repository for the Inspec profile separately, you could directly run the Inspec checks below.
inspec exec https://github.com/XXXXXX/inspec-profile-aws-tc-
k8s.git -t aws:// --input bucketname="s3_bucket_name"
You can use any cloud resource from the list to run the profiles on your Cloud service.

