Chef InSpec is an open-source framework for creating, testing, and applying compliance and security policies through human as well as machine-readable language. Chef InSpec compares the actual state of your system with the desired state, detects violations, and displays findings as a report that offers insights for remediation.
Setting up the Environment
InSpec resource pack uses the Azure Ruby SDK (Software Development Kits), making it easy to write tests for resources in Azure.
Prerequisites
To allow InSpec to authenticate your Azure account, you will need to create an Azure service principal.
For this, you must have the following information:
TENANT_IDCLIENT_IDCLIENT_SECRETSUBSCRIPTION_ID
~/.azure/credentials The credentials file should have the following structure:
[<SUBSCRIPTION_ID>]
client_id = "<APPLICATION_ID>"
client_secret = "<KEY>"
tenant_id = "<DIRECTORY_ID>"
These values must also be stored in an environment variable. If you use dotenv, you can save these values in your own .envrc file. If you do not use dotenv, then you can create an environment variable in the way that you prefer.
Before you test your infrastructure, create a new profile by executing the command below. This will create a new folder in your current directory which contains several new files and folders related to InSpec profiles.
$ inspec init profile azure_profile
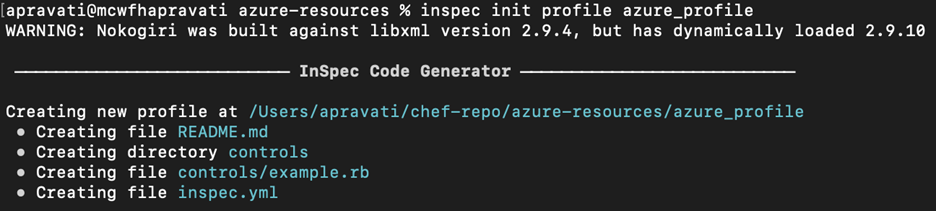
Edit the newly created inspec.yml file which is found in the profile directory and change default values according to needs.
name: azure_profile
title: Check resource group
maintainer: Akshay
copyright: Akshay
copyright_email: Akshay@chef.com
license: Apache-2.0
summary: An InSpec Compliance Profile
version: 0.1.0
depends:
- name: inspec-azure
url: https://github.com/inspec/inspec-
azure/archive/master.tar.gz
supports:
- platform: azure
Besides the profile, you will need at least one Inspec control which defines what InSpec is going to test in your subscription. Controls are put in the controls folder of your newly created Inspec profile.
Default.rb
control 'azurerm_virtual_machine' do
title "Check resource group"
desc "Check if resource group is present"
describe azure_resource_group(name: 'azureubuntu_group') do
it { should exist }
end
end
The above scenario checks if the resource group “azureubuntu_group” exists in the given subscription. You can also easily check whether your subnet has a network security group assigned and if this network
security group allows SSH and RDP traffic from the internet.
Once you have created at least one control, run a check to see if your profile is valid or if it has any errors or warnings.
$ inspec check azure_profile
WARNING: Nokogiri was built against libxml version 2.9.4, but
has dynamically loaded 2.9.10
Location: azure_profile
Profile: azure_profile
Controls: 1
Timestamp: 2022-09-08T12:17:37+05:30
Valid: true
To check for any syntax error, use this command
$ cookstyle -a
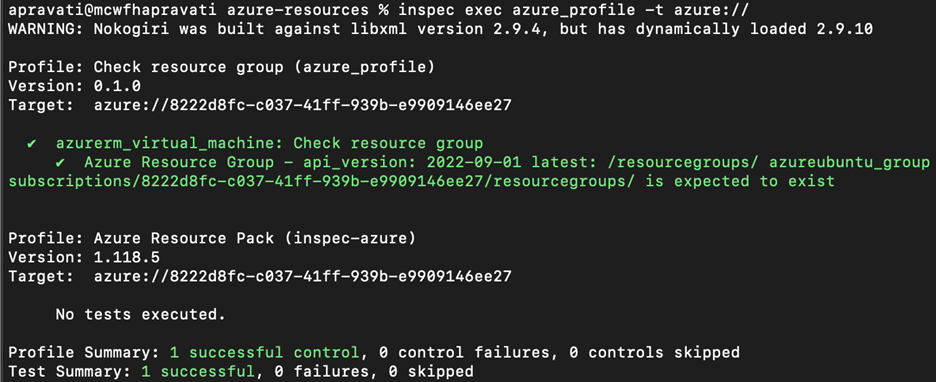
To run the checks against your Azure account, execute your InSpec profile with Azure as the target provider.
$ inspec exec azure_profile -t azure://
Inspec is a fast and easy-to-use tool that can help you implement Compliance as Code. By supporting many different platforms, it enables organizations to use one tool for compliance testing throughout their heterogeneous
infrastructure landscape. With InSpec, you can have tests running continuously using a CI pipeline so that any changes to your (Azure) cloud infrastructure are tested in a non-prod environment and then promoted to production.

