Containers are integral to the modern cloud-native stack. Containers are lightweight yet encapsulate everything needed to run an application, from executables and libraries to application code and configuration files. Containers have transformed application development and deployment with increased portability, efficiency, and extensibility.
What is OpenShift?
The popularity can be attributed to some of the benefits it offers:
- Built-in security and monitoring capabilities, multi-tenancy features and integrated storage.
- Increased DevOps productivity and faster development cycles as it reduces the time spent managing Kubernetes, including the underlying nodes and control plane.
- Improved release velocity due to streamlined CI/CD processes and efficient CI/CD pipeline management.
The diagrams below illustrate the layered system of the OpenShift platform. The Docker service creates container images, while Kubernetes provides container orchestration and cluster management capabilities. The “etcd” stores data about each object in a secure key-value format and each object can be accessed using REST APIs.
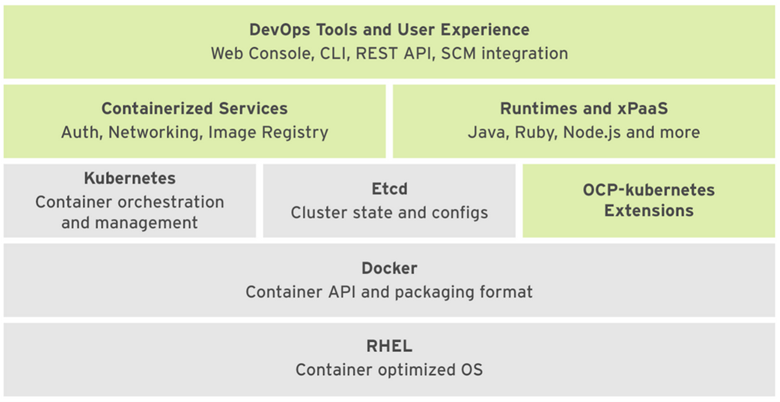
Figure1: OpenShift Container Platform ComponentsOpenShift Security Challenges
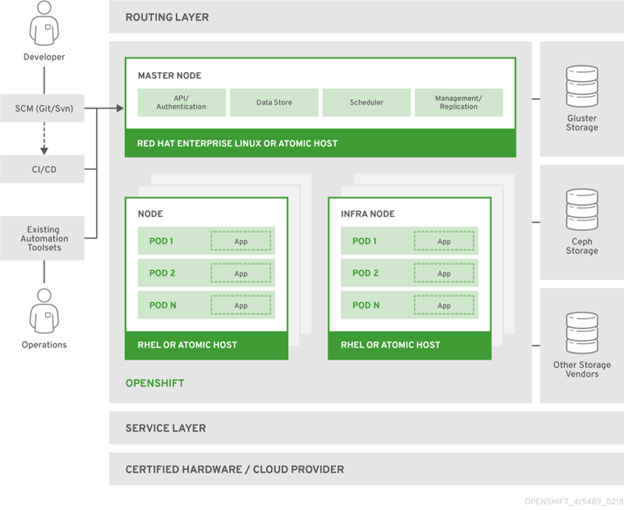
Figure 2: OpenShift Container Platform Architecture Overview (source: docs.openshift.com)
OpenShift Security Challenges
OpenShift is a secure platform that provides several built-in security features by default. It enforces security policies and best practices at every level in the cloud-native stack. However, as with any cloud-based platform, maintaining security and compliance posture is a shared responsibility. There will inevitably be security risks that require additional measures to prevent compromising application security. Some of the common security challenges that need to be addressed in an OpenShift environment are:
Misconfigurations
Misconfigurations are very common in large, complex IT environments where IT admins are managing multiple cloud accounts with different configurations. In such scenarios, incorrect security settings or unintended changes in the configuration can create vulnerabilities in the OpenShift platform, exposing the platform to potential threats.
User Access
Compliance
Scaling Security
Container Image
Implementing OpenShift Container Security with Chef
Chef container security enables you to:
- Define Policies: Determine security goals and create policies or follow standard benchmarks like the CIS OpenShift benchmark.
- Scan Configuration: Audit the configuration of OpenShift environments to identify security risks or compliance violations based on your policies.
- Analyze and Alert: Assess audit results, analyze and prioritize failure and then alert stakeholders.
- Remediate: Resolve security and compliance issues and repeat the audit process regularly.
Chef container security solution offers a comprehensive toolset to secure CI/CD pipelines, continuously scan containers for security risks, manage compliance posture and gain unified visibility into the OpenShift environment. All this can be done in four easy steps:
- Step 1: Integrate your OpenShift environment.
- Step 2: Select the CIS OpenShift Container Platform Level 1 and/or Level 2 profile.
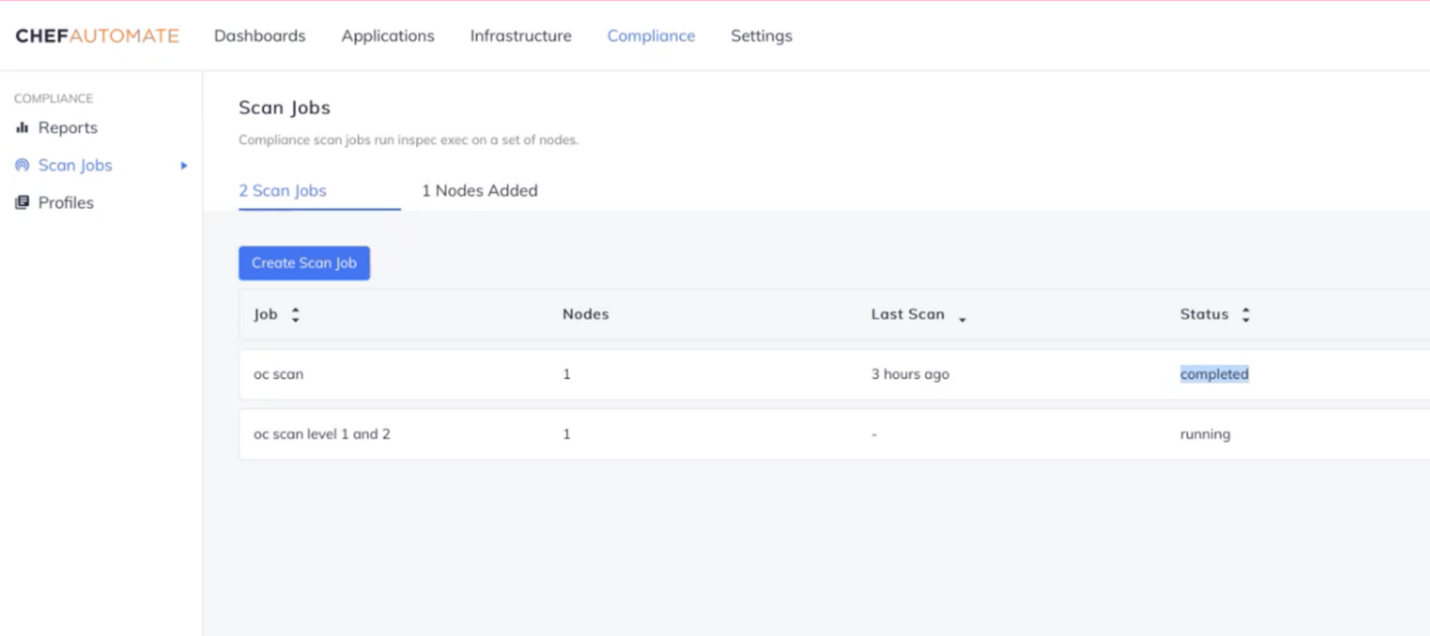
- Step 3: Schedule regular scanning of the OpenShift integration.
- Step 4: Access the report to view the security posture of your OpenShift environment.
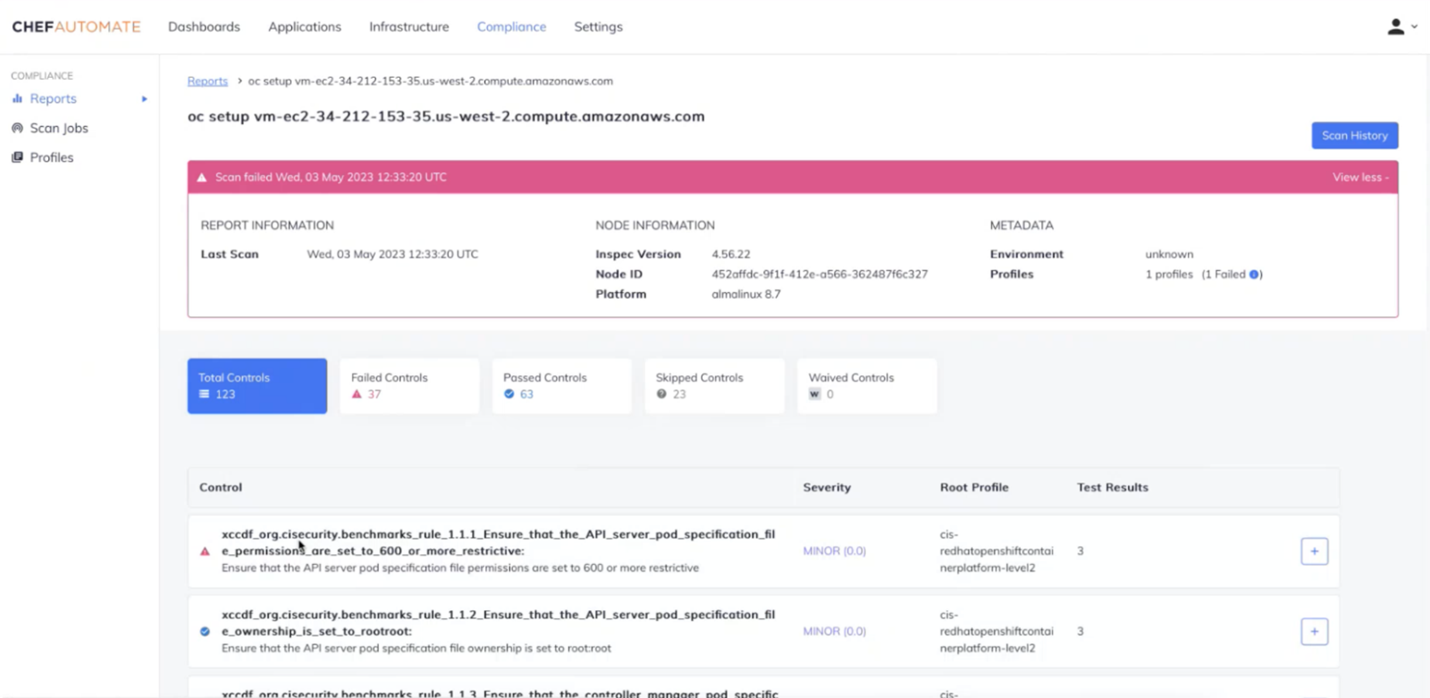
These steps will ensure continuous compliance and security for OpenShift environments through Chef’s container security features:
1. Detect misconfigurations continuously.
2. Scanning control plane components such as:
- Master node configuration files - secure API server, scheduler service, etcd service, and container network interface.
- Secure “etcd” data directory, admin credentials, Kubeconfig file, and Key files.
- Controller manager and scheduler.
3. “etcd” security
4. Scan and secure control plane configuration – authentication and logging.
5. Scan and secure worker node configuration – Kubelet and configuration file.
6. Enforce policies - RBAC and service accounts, Pod security policies, network policies and CNI, and secrets management.
Summary
OpenShift, along with Kubernetes, simplifies container stack management, automates installation and upgrades and speeds up development workflows. Chef container security extends OpenShift security capabilities with a range of additional security functionality to help:
- Maintain continuous compliance across the entire IT estate with built-in compliance for OpenShift.
- Detect and prioritize misconfigurations across OpenShift environments.
- Enforce internal compliance policies or customized policies for misconfiguration detection and internal best practices.
- Remediate using remediation guidance for correcting policy violations.
To learn more about securing OpenShift with Chef, listen to the on-demand webinar here.

